SSH Port Forwarding
SSH port forwarding is a method of allowing secure, encrypted connections to traditionally non-encrypted services, such as POP3 for email, NNTP for news, and even Telnet for remote hosts without their own SSH encrypted access.
With this method of connecting to the servers, you would open a SSH connection to “tunnel” a local port to a remote server’s port, then set your application software to connect to your own local port. This way, any passwords or data being transmitted at your own location (a wireless access point for instance) would be sent over the encrypted SSH connection rather than out in the “open” (though the final server-to-server step is indeed unencrypted by the nature of the forwarded protocols).
Port Forwarding on Unix® Machines
The Mac OS X, Linux, UNIX, and similar systems, including Cygwin for Windows®, provide the same interface for accessing the ssh command, so the instructions for these environments are identical:
| ssh -L LPORT RHOST:RPORT SSHHOST | ||
| Where… | ||
| LPORT | = | Local Port, a port on your machine |
| RHOST | = | Remote Host, server to connect to |
| RPORT | = | Remote Port, port on the remote host |
| SSHHOST | = | SSH Host; “eskimo.com” for our customers. |
Unix-based servers require “root” permissions to forward locally privileged ports (usually 0-1023), so setting up ports outside this range under a regular user’s permissions is better for your system’s security. Also using non-standard ports locally may help avoid software infections from abusing your forwards.
While it’s more secure to only have actively-used ports open at any given time, any number of forwards can be setup on a single connection. For instance, to only open a secure POP3 port on mail.eskimo.com:
| ssh -L 5110:mail.eskimo.com:110 eskimo.com |
To open both POP3 and NNTP in the same manner:
| ssh | -L 5110:mail.eskimo.com:110 \ |
| -L 5119:news.eskimo.com:119 eskimo.com |
You can verify that the ports have been opened for forwarding by adding ‘-v’ (for ‘verbose’) to the ssh arguments:
| ssh -L 5110:mail.eskimo.com:110 -L 5119:news.eskimo.com:119 -v eskimo.com…eskimo.com: Connections to local port 5110 forwarded to remote address pop3.eskimo.com:110 eskimo.com: Connections to local port 5119 forwarded to remote address news.eskimo.com:119… |
Scroll below to “Using Forwarded Ports”.
Port Forwarding on Windows® Machines
The steps above will configure the Cygwin environment. For others, using the same example port numbers and servers as above, two common applications are PuTTY and TeraTerm Pro (both free). Others may be available with similar configuration terms to find in their documentation.
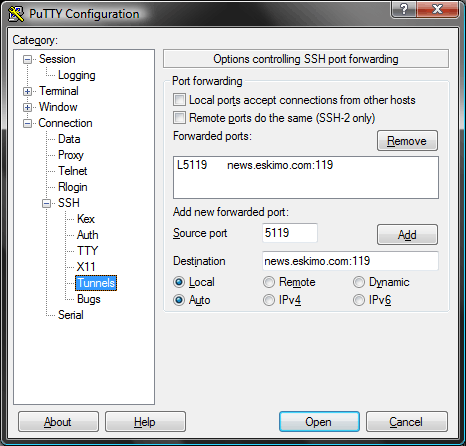
Before starting the SSH connection to eskimo.com, go to the “Tunnels” panel (within “Connection / SSH” in case it’s collapsed to “[+]” expandable lists), make sure the “Local” option is selected (currently on the bottom of the window), and for an NNTP example forward, use:
| Source Port: | 5119 |
| Destination: | news.eskimo.com:119 |
Click “Add” to add this to the configured tunnels/forwards. The screen below shows both the typed and added versions:
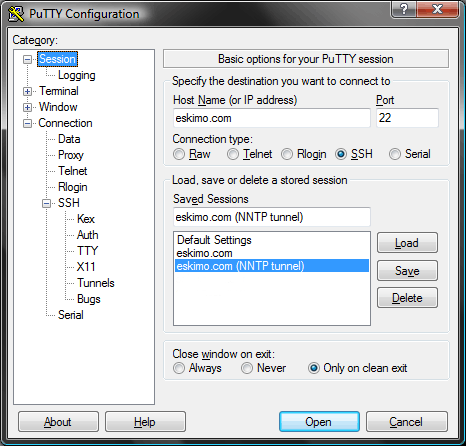
Back in the “Session” portion (currently the top selection in the list) preconfigured sessions can be saved for future use before connecting by typing a name and choosing ‘Save’. Below, there are both standard non-tunnelled SSH and NNTP-tunnelled saved SSH sessions. Saved sessions can be started with a double-click on the appropriate name.
When your session is connected and logged in, you can right-click the title bar of PuTTY’s window and select “Event Log” to verify that the forward has been setup:
| …(date and time) Local port 5119 forwarding to news.eskimo.com:119… |
TeraTerm Pro with SSH Extension:
“ttssh” uses a command line system similar to the Unix method shown above, with a slightly different argument set:
ttssh
eskimo.com:22
/ssh-L5110:mail.eskimo.com:110
Notice that ‘-L’ has become ‘/ssh-L’ and there is no space between it and the port information. Also be sure you specify port 22 (ssh) on eskimo.com. The order of the arguments may be needed as shown above (I’ll check on that…order may not be required).
Alternatively, you can use the configuration window listed under Setup / SSH Forwarding.
Using Forwarded Ports
Using these forwards requires setting your software’s preferences to use the appropriate local ports instead of the unencrypted originals. For example, using Mozilla Thunderbird’s mail and news settings:
| Instead of… | Incoming Mail: | mail.eskimo.com, port 110 |
| Use… | Incoming Mail: | localhost, port 5110 |
| Instead of… | Newsgroups: | news.eskimo.com, port 119 |
| Use… | Newsgroups: | localhost, port 5119 |
Services that could be forwarded for this reason may be anything that requires username/password authentication (email and news examples are unencrypted once sent/posted, but your own password is secured) or otherwise single-port unencrypted connections, including:
| Telnet | …elsewhere… | 23 |
| SMTP | mail.eskimo.com | 25 |
| POP3 | mail.eskimo.com | 110 |
| NNTP | news.eskimo.com | 119 |
We do offer SSL-encrypted POP3 here as well; this forwarding version could be useful where that is not available.
